Recent cyber attacks have underscored a long-standing issue for cyber insurers: How much protection can and should insurance provide when the perpetrators of such attacks are linked to nation states? The final report in the The Geneva Association’s and IFTRIP’s series on cyber terror and cyber war examines the insurance industry’s ability to underwrite these risks and the role of public-private partnerships in future insurance solutions.
Hostile cyber activity and insurance
Traditional policy exclusions for war or war-like incidents fail to adequately capture situations where nation states are suspected of being behind an attack or at least providing a safe harbour for the hackers, especially if the motives for the attack are unclear. Such issues of attribution and characterisation create significant contractual uncertainty for insurers, which has only added to the recent tightening in cyber insurance market conditions.
More granular classifications of cyber incidents – including hostile cyber activity (HCA) terminology, which provides for a lower burden of proof for state involvement than current, widely-used definitions – will help provide greater clarity for insurers and increase comfort levels with their exposure. But market acceptance of tighter policy language over insured cyber incidents takes time and even then, will likely only go so far.
The latest cyber incidents highlight the residual challenges in creating clear-cut, definitive boundaries around what legitimately falls within HCA and what does not. Nation-state involvement varies widely, from reported tacit sponsorship, including fostering an environment for developing sophisticated yet easy-to-use malware (e.g., the attack on Colonial Pipeline), to alleged, outright supervision and resourcing of hacking campaigns by a sovereign government (e.g., SolarWinds). In such circumstances, some of the difficulties of direct attribution for HCA resurface, particularly if state actors linked to criminal gangs use false-flag tactics to hide their traces, blame others or otherwise undermine any international consensus about the ultimate source of the attack.
Quantifying cyber risks remains challenging
Advances in modelling and the quantification of cyber risks, as well as reinsurance availability and other mechanisms to share risks, will be key to encouraging both incumbent and prospective insurers to offer increased coverage for HCA and other malicious cyber activity. Unlike for natural catastrophe perils – for example, hurricanes or man-made disasters such as terrorist attacks – cyber perils have no geographical borders; the whole world is potentially one cyber catastrophe zone. Beyond issues of attribution and characterisation, assessing the frequency and severity of HCA, especially the potential for large accumulated losses, remains a particularly serious challenge.
Deterministic scenario analysis suggests some malicious cyber incidents, such as a temporary disruption to cloud services, might trigger economic losses broadly comparable with some historical natural catastrophes (Table 1). But more extreme and long-lasting cyber attacks, including a widespread IT or operational infrastructure outage or failure, could generate significantly larger expected losses. Moreover, the uncertainty surrounding such estimates is very large, meaning that total potential losses could be significantly higher than these ‘guesstimates’, easily exhausting re/insurers’ risk-absorbing capacity. This is especially true of HCA incidents where ambiguity over hackers’ motives, tactics and threat vectors, as well as the possibility for relatively minor, isolated attacks to escalate towards full-out cyber warfare, only add to the complications of quantifying cyber risks.
The role of a government backstop
Advances in gathering cyber threat intelligence, including collaboration across firms and governments, will boost risk awareness and preparedness, important elements in building cyber resilience. Such information will enable insurers to detect vulnerabilities and foster improvements in modelling cyber risks. Likewise, progress by law enforcement agencies in tracing and pursuing the perpetrators of an attack and recovering extorted funds may go some way to deterring cyber criminals and increasing insurers’ comfort levels in offering risk-absorbing capacity.
Ultimately, however, the systemic characteristic of some cyber risks, in particular the potential for multiple losses from a single event or a campaign of attacks linked to HCA, mean that the scale of accumulated losses may exceed levels that can safely and sensibly be absorbed by the private re/insurance sector. To some extent too, the latest spate of attacks can be seen as near-misses; if circumstances had transpired differently the losses could have been much worse.
Echoing current debates over pandemic-related risks, consideration should thus be given to government-backed solutions to finance these tail cyber risks in order to boost economy-wide resilience. A well-designed public-private partnership (PPP) could increase protection capacity and still encourage cyber market innovations to extend cover for HCA risks. This should not simply be a fiscal solution but also seek, through collaboration with insurers, to promote the adoption of cybersecurity best practices – including taking out appropriate insurance – to reduce societal vulnerability to such risks.
Designing a public-private partnership
Designing such government-backed solutions is complex. Important considerations for any PPP include whether the scheme is mandatory or voluntary, coverage is parametric or indemnity-based or if the scheme is founded upon mutuality or solidarity principles. From a fiscal and feasibility viewpoint, it will also be necessary to ensure that adequate measures are adopted to fund the scheme and to ensure sufficient capital, either on a pre- or post-event basis. There will be trade-offs in adopting particular scheme features and difficulties in calibrating how much of the peak losses should be shared among policyholders, private (re)insurers and governments (Table 2).
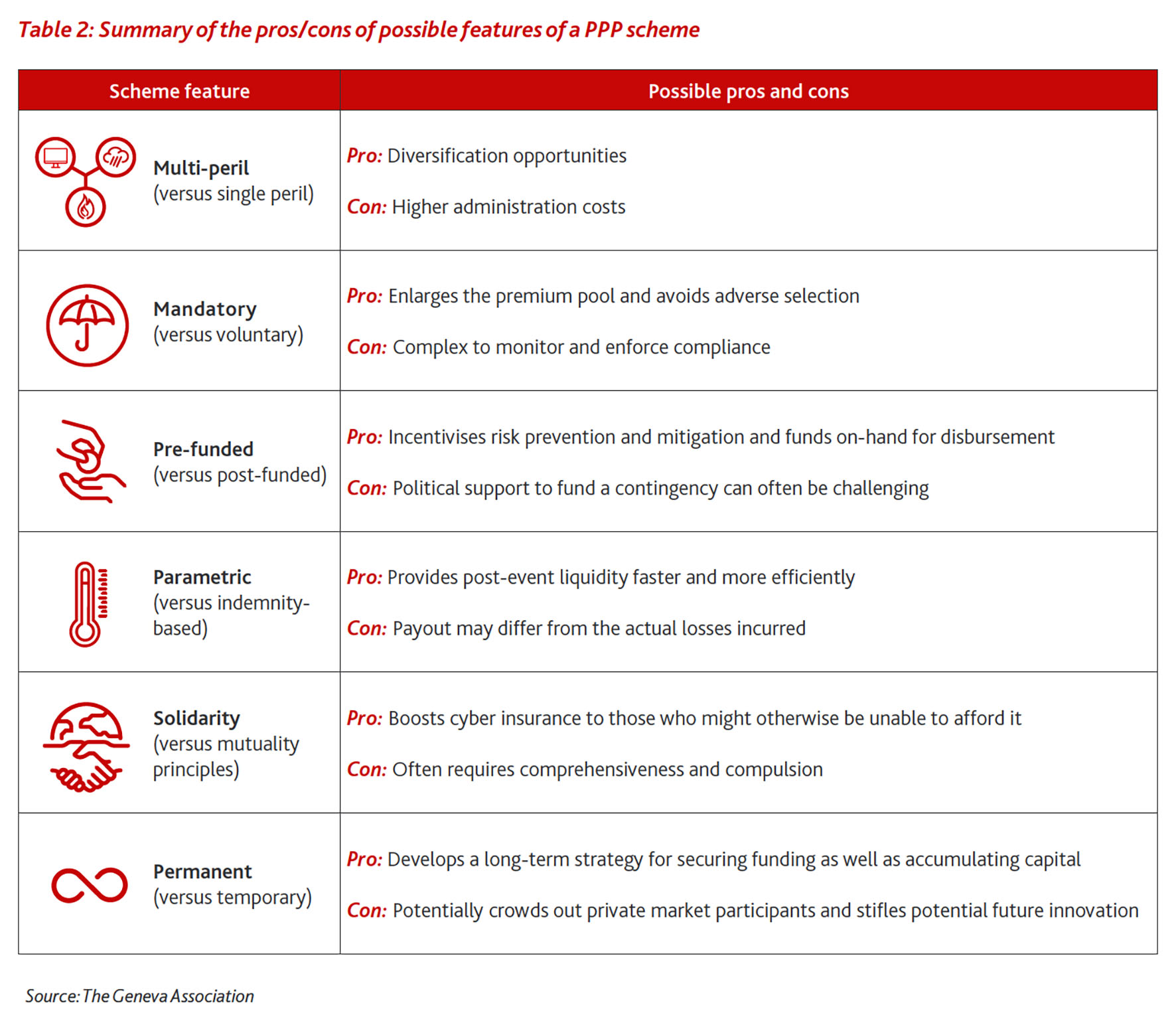
Such design challenges are amplified at the international level. Ideally, given the interconnected and global nature of cyber risks, cooperative international solutions to cover HCA risks would be an option. However, legal limitations, cultural differences, access to capital and doubts about the willingness of individual governments to share risks across different jurisdictions mean that global solutions remain practically infeasible, at least in the short term. As a result, priority should be given to developing domestic PPP solutions for large-scale cyber risks.
The insurance industry has come a long way in its understanding of cyber terrorism, HCA and cyber war and assessing how to insure such risks. To expand the limits of insurability, insurers need to be proactive in assessing feasible options for sharing cyber risks, including with governments via PPPs. Such collaborative efforts between insurers and governments will enable cyber protection gaps to be narrowed and ensure the full societal benefits of cyber space can be realised. A
Dr Rachel Anne Carter is managing director with Carter Insurance Innovations and Mr Darren Pain is director cyber and evolving liability with The Geneva Association.